Why Bad UX Endangers IT Security (and Inclusion)
Sometimes the algorithm serves up things in your timeline that you initially mistake for satire. That’s how I felt recently with a find by Pascal Wegner on X. He shared a screenshot from the Federal Network Agency (Bundesnetzagentur) that seemed too absurd to be true.
I had to see it for myself, so I went to the website, opened developer tools, and there it was: that moment of disbelief. A captcha grinned back at me. Those annoying letter puzzles meant to prove you're not a robot.
The Instruction: “Please enter the text in capital letters and without spaces.”
Sounds standard, right? But the background was anything but: A look at the source code confirmed the suspicion. The solution to the puzzle was right there, in plain text.
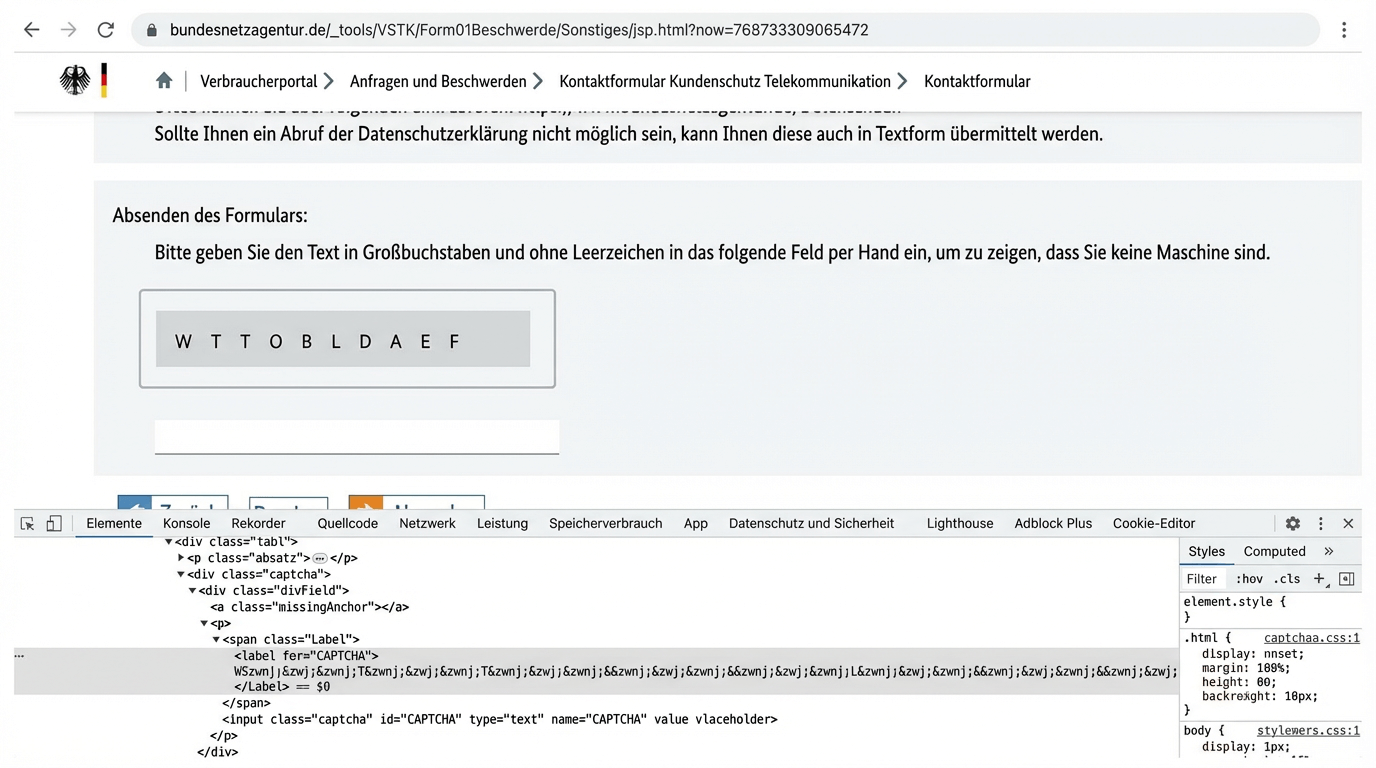
To make it “harder” for bots, they had merely mixed invisible separator characters between the letters in the code.
The Result: An “Anti-Captcha” A task that is tedious for humans but solvable for machines in milliseconds.
I shared this on LinkedIn, and the post went through the roof with over 150,000 impressions and more than 50 comments. But just like with the AOK, where "End my life" became a button I wrote about here, this is more than just a funny fail. It is a symptom of a deeper problem in the German IT landscape.
We invest massive resources in compliance and privacy statements. But in practical implementation, we build digital Potemkin villages. Security is often seen as something that “must hurt” to be effective. And that’s exactly why solutions arise that are neither secure nor accessible.
And honestly? This isn't just a tech problem. It's a cultural risk.
1. Hiding the key isn't a security strategy
In the physical world, no one would put their front door key under the doormat and hope the burglar doesn't look there. Digitally, we do exactly that when we offload validation logic to the client (the browser).
The Federal Network Agency tried to hide the solution using invisible control characters (‌ / Zero-Width Non-Joiner).
The Problem: A bot doesn’t “look” at the page like a human. It parses the code. For a script, removing control characters is a one-liner.
We are trying to patch a frontend problem here, even though the architecture behind it (server-side validation) is missing. This costs trust. When an authority responsible for critical infrastructure leaves such gaps, citizens rightly ask: What about the really important systems?
2. Accessibility isn't "nice to have"—it's the law
Here it gets critical. Since the Accessibility Reinforcement Act (BFSG), which took full effect in June 2025, and the BITV 2.0 applicable to authorities, exclusion is no longer a trivial offense.
This captcha is an absolute showstopper for people with disabilities:
- Screenreader Chaos: Imagine you are blind and having the page read to you. The screen reader encounters the label
W‌T‌T.... Either it reads letter by letter with cryptic pauses, or it chokes on the control characters. The instruction “Type without spaces” becomes a cognitive high-performance task if your reading tool doesn't tell you clearly what is actually there. - Cognitive Barrier: The instruction requires extra cognitive effort (observe capital letters, ignore spaces, recognize cryptic character sequences). For people with learning difficulties or dyslexia, this is an unnecessary hurdle.
- Missing Alternative: Where is the audio button? Where is the alternative for people who cannot see the image?
The irony is bitter: We lock out real people with disabilities to ward off bots, and the bots are the only ones who get through without barriers because of the source-code fail.
3. Real security is invisible
Perhaps even more exciting than the technical aspect is the misconception that security and User Experience (UX) are opponents.
In many minds, the mindset prevails: “If it is to be secure, the user must suffer.” That’s why we accept clicking traffic lights and cryptic text inputs.
The reality of 2026 looks different. Modern bot defense (like Cloudflare Turnstile or proof-of-work approaches) happens in the background.
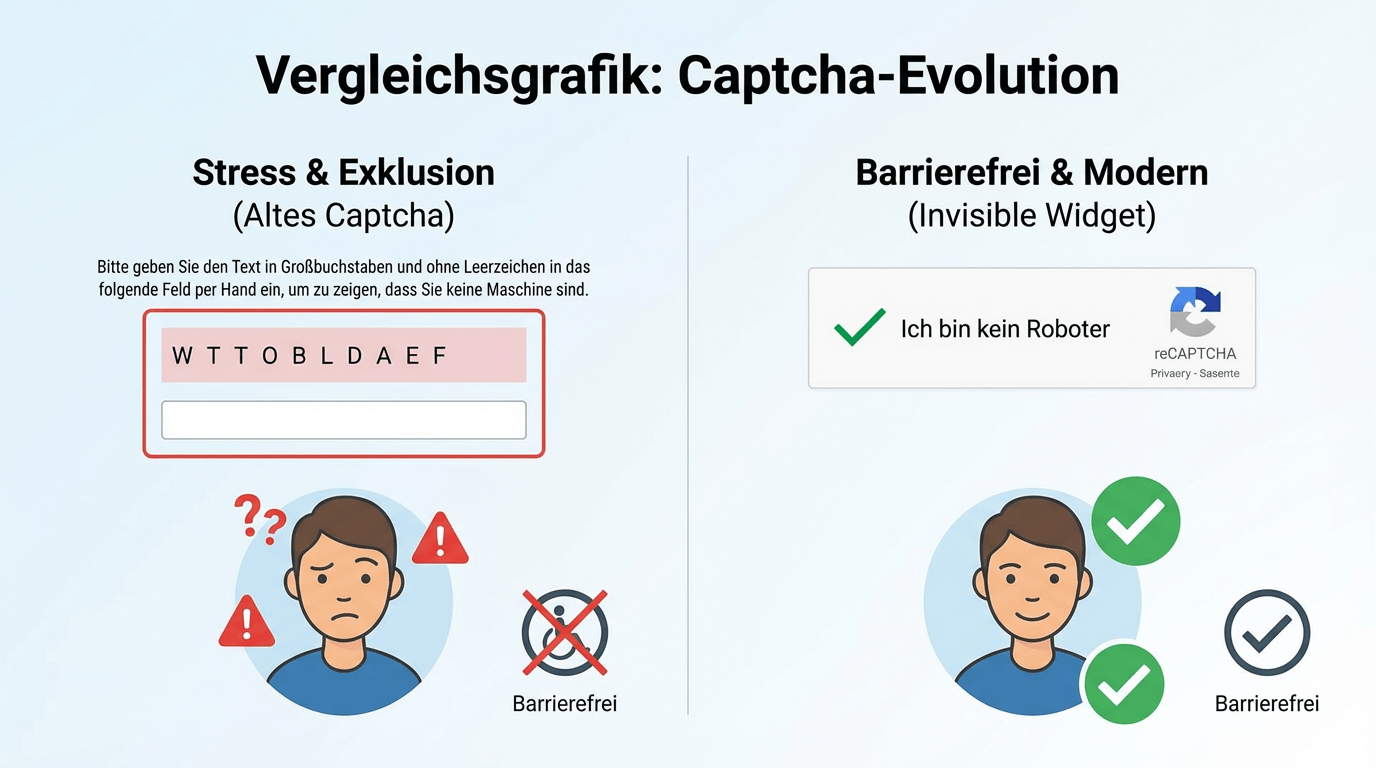
Good security does not hinder the user. It validates quietly.
The BNetzA example shows the “Not Invented Here” effect: out of fear of GDPR hurdles with established external providers, a custom solution was cobbled together. The result is the worst of all worlds: maybe okay under data-protection law, but ineffective in terms of security and a disaster in terms of inclusion.
Roadmap: Away from the "Fax-Mindset"
Anyone who still asks for text to be typed has actually already lost the fight against AI bots. AIs can recognize text and images better than we humans can by now.
The solution lies in a change of perspective: Make the browser do the work.
You don't need a 700,000 Euro consultant budget. Start with the basics:
- Server-side validation is mandatory The solution must never leave the server before the user has entered it. Never trust the client (browser).
- Accessibility First Check every security measure: Can a blind user operate this? If not, the solution is illegal and unethical. Modern “Invisible Challenges” are inherently more accessible because they require no interaction.
- Don't roll your own Crypto The golden rule of IT security. Do not build your own security mechanisms if you are not a cryptographer. If you reinvent the wheel, it usually ends up square, and trips up screen readers.
- Pentesting & User Testing Invite external experts. A single test with a screen reader or a look by a security student would have been enough to make this house of cards collapse. Operational blindness is the biggest security risk.
Conclusion: Courage to Professionalize
The fail of the Federal Network Agency causes laughter on LinkedIn (“Hold my fax machine for a second”). But it painfully shows that we often still misunderstand digitalization.
We must stop understanding digitalization as the “digitization of paper processes”. A digital form in the year 2026 must be safe and accessible to everyone.
Companies and authorities that think Security, UX, and Accessibility together create systems that are used. They replace frustration with trust, and ensure that the front door is really locked instead of just putting the key under a transparent doormat.
Further Reading & Modern Solutions
- Original Source: Pascal Wegner's Post on X
- Cloudflare Turnstile: Privacy-first alternative to CAPTCHA
- Google reCAPTCHA v3: Invisible fraud detection
- mCaptcha: Proof-of-Work based CAPTCHA system (Open Source)
- W3C Web Accessibility Initiative (WAI): CAPTCHA Alternatives and Thoughts